Baiting Facebook Groups


What’s on this page
CTM360 discovered an ongoing fraudulent activity on Meta's social media platform, ‘Facebook’.
Threat Overview
While conducting fraud hunting exercises, CTM360 discovered an ongoing fraudulent activity on Meta's social media platform, ‘Facebook’. This particular scam involves scammers using Facebook public groups to disseminate fraudulent schemes. These groups are created solely to bait victims. By leveraging these groups, the scammers can reach a large audience that shares common interests or belongs to specific regions. Unfortunately, this fraudulent activity has resulted in financial losses for many unsuspecting individuals.


Fraud Methodology
The scammers begin by either scouting Facebook groups OR creating new groups that serve the scammer's goal, aiming to identify the target audience. This is likely done through various criteria such as:
- Page Topic: the main drive and title that define the overall niche.
- User Interests: the general interest and posts shared in the group by the members.
- Targeted Region: the location where the scammer wants to target the users.
- Scammers are carrying their scams through Facebook and specifically through Facebook groups to abuse its private nature with the ability to mask the profile’s name causing a noticeable rise in fraudulent activities advertised with untraceable users - through the "Anonymous Participant" feature in Facebook Groups.
- Within the suspicious posts, scammers are claiming to provide bogus services like:
- Fraudulent Payment Installments
- Loans or loan restructuring
- Issuance of Credit Cards with high limits
- Fake Job Posting
- Stolen Gift cards
Why Should Organizations Be Concerned?
To reflect legitimacy of the fraudulent promotional post the scammers abuse genuine company name or genuine product brands.
Scammers adopt various tactics, such as presenting themselves as authentic sellers offering enticing deals on products. So they are “impersonating” your organization, brand or identity of your executive management.
Their goal is not to deliver the promised items at all or to provide counterfeit goods. Hence they impersonate well-known brands, celebrities, or even users' friends within these groups, leveraging these false identities to deceive individuals into disclosing sensitive information or making monetary transactions.
One variation of the scam posts claims to host free giveaways or contests. These seemingly attractive offers often serve as a guise to harvest personal information or involve users in deceptive activities. The other scam cases range from inquiries about installment options, salary transfers, credit card applications, loans, and job opportunities to scams like Advance-Fee Fraud.
The unauthorized use of an organization's brand name in posts within such Facebook groups poses a significant concern. At minimum it has implications on reputation, furthermore your customers could suffer financial losses or compromise their personal information, leading to broader implications for both the organization and the affected individuals.
Threat Impacts
The fraudulent posts published in these groups can have various threat impacts on the users such as:
- Financial Loss: These posts often involve fraudulent loan offers that target individuals who are in need of financial assistance. Scammers may request upfront fees or personal information, promising a loan that never materializes.
- Expose Personal Information: When users share personal and financial information in response to fake offers in Facebook groups, there is a risk that this information may be shared or sold to third parties without their consent.
- Phishing Attack: Some loan scams may involve indirect phishing attempts, where scammers might trick individuals into providing their login credentials or other sensitive information through fake loan application forms or websites.
Recommendations
For Businesses:
- Spread Awareness: Conduct awareness campaigns on official social media to educate customers about such scams.
- Active Monitoring & Takedowns of Baiting Facebook Groups: Such baiting groups should be actively monitored and any infringement identified related to your brand should be reported to vendors for further actions such as Takedown.
For Individuals:
- Be cautious with personal information: Avoid sharing personal information in Facebook groups, especially if the posts seem suspicious or potentially fraudulent. Protect your identity and be wary of any requests for sensitive information.
- Don't Pay Upfront Fees: Legitimate lenders typically deduct fees from the loan amount or include them in the repayment plan. Be cautious of these scammers who request upfront fees before providing the loan. This is a common red flag for scams.
Recent Blogs

Microsoft Joins the Push: DMARC Mandatory for High-Volume Senders Starting May 2025
Overview
The fight against email-based threats is intensifying. Following the lead of Google and Yahoo, Microsoft has officially announced the mandatory implementation of email authentication protocols, SPF, DKIM, and DMARC, for high-volume email senders, effective May 5, 2025. Domains sending over 5,000 daily emails to Microsoft's platforms, including Outlook.com, Hotmail.com, and Live.com, will be required to authenticate their messages. Initially, non-compliant messages will be redirected to recipients' Junk folders, with eventual total rejection expected if compliance isn't achieved. This enforcement represents a critical step in securing global email communications from spoofing and phishing threats (Microsoft Tech Community).
Understanding Email Authentication
Email authentication has become essential in combating increasingly sophisticated phishing and spoofing attacks. Three core standards have been adopted widely:
- Sender Policy Framework (SPF: RFC 7208): Verifies the legitimacy of the sending mail server, ensuring messages originate from authorized infrastructure. SPF helps prevent sender address forgery by defining authorized sending sources in DNS records.

- DomainKeys Identified Mail (DKIM: RFC 6376): Cryptographically signs email messages, allowing recipients to confirm message content hasn't been altered in transit. DKIM leverages public-private key pairs to ensure message integrity and authenticity.
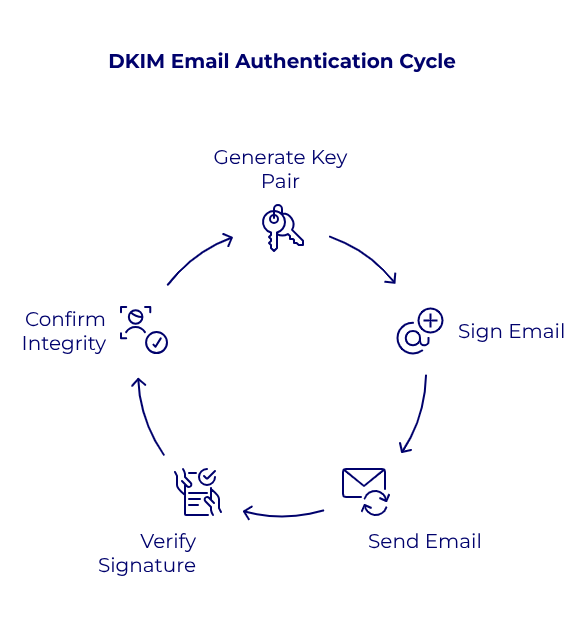
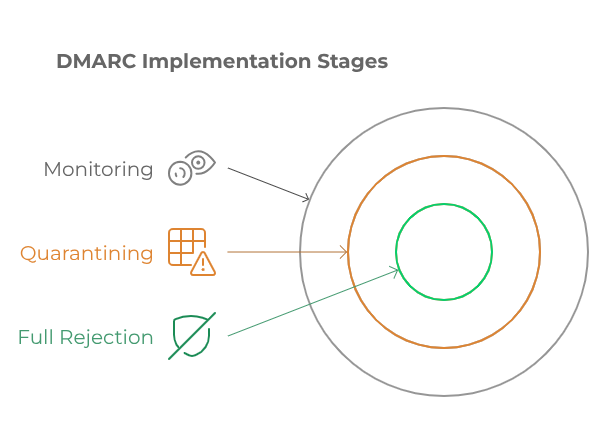
- Domain-based Message Authentication, Reporting, and Conformance (DMARC: RFC 7489): Combines SPF and DKIM to enforce domain alignment, verify authenticity, and provide reporting mechanisms for senders to track email usage and potential abuse. DMARC is recommended to be implemented in three incremental stages: initial monitoring (p=none), intermediate quarantining of suspicious messages to test the policy impact (p=quarantine), and full rejection of unauthorized emails to achieve DMARC compliance (p=reject).
Email Content and Delivery Best Practice Guidance
To help the email ecosystem thrive and ensure that legitimate communications reach users' inboxes, major providers like Google, Yahoo, and Microsoft have released a unified set of technical and content-based requirements. This section consolidates these guidelines into a single resource for senders seeking to avoid spam filtering and maintain high deliverability rates.
1. Message Headers & Structural Integrity
2. Content Hygiene and Formatting
3. Infrastructure and Technical Configuration
4. Recipient List Management
5. Engagement and Complaint Monitoring
6. Summary Recommendations
- Align headers and domains with clear, professional identities.
- Respect opt-in and unsubscribe behaviors with transparent mechanisms.
- Structure content to be clean, concise, and free of deceptive or spammy characteristics.
- Maintain technical hygiene through DNS, TLS, SPF limits, and ARC usage.
- Monitor sender reputation and user engagement continuously.
Immediate Impact and Risks of Non - compliance
As of May 2025, domains that fail SPF or DKIM checks or lack a correctly configured DMARC policy with alignment will risk having their emails marked as spam or not delivered at all. Misalignment occurs when the domain used in the message's "From" address doesn't match the domains authenticated by SPF or DKIM.
Organizations failing to comply face significant risks, including diminished deliverability rates, compromised customer trust, and increased susceptibility to impersonation attacks. These impacts directly affect an organization's reputation, customer engagement, and potentially, its revenue.
Actionable Recommendations for Immediate Implementation
To effectively prepare for these mandatory standards, organizations should:
- Audit current DNS records: Utilize tools such as "dig" or Google DNS to verify SPF, DKIM, and DMARC records.
- Begin with Monitoring (p=none): Initially deploy DMARC in monitoring mode to understand email flows and detect anomalies without risking legitimate email delivery.
- Gradually enforce stricter policies: Move from quarantine to full rejection while monitoring.
- Ensure domain alignment: "From" domain must match what’s authenticated via SPF or DKIM.
- Maintain email hygiene: Clean lists, include a clear opt-out option, and avoid using misleading subject lines or headers.
Start Your DMARC Journey with CTM360 Free Community Edition
To support organizations navigating these changes, CTM360 offers a complimentary zero-cost Community Edition platform. It allows comprehensive monitoring, management, and enhancement of your DMARC records and email authentication setup. This proactive approach helps organizations reduce risks associated with impersonation attacks and maintain reliable email communication.
Join CTM360 Community Edition today, no hidden costs, simply real security.
Reference:
Disclaimer:
The information contained in this document is meant to provide general guidance and brief information to the intended recipient pertaining to the incident and recommended action. Therefore, this information is provided "as is" without warranties of any kind, express or implied, including accuracy, timeliness, and completeness.
Consequently, under NO condition shall CTM360®, its related partners, directors, principals, agents, or employees be liable for any direct, indirect, accidental, special, exemplary, punitive, consequential, or other damages or claims whatsoever including, but not limited to loss of data, loss in profits/business, network disruption...etc., arisina out of or in connection with this advisory.
For more information: Email: monitor@ctm360.com Tel: (973) 77 360 360

Securing Browsing Extensions
Summary:
In December 2024, hackers compromised at least 35 Google Chrome extensions, affecting approximately 2.6 million users. The attack exploited phishing emails sent to developers, masquerading as Google policy violation notices. These emails tricked developers into granting permissions to a malicious OAuth application named
“Privacy Policy Extension.
” Once authorized, the attackers gained control over the extensions, injecting malicious code to steal user data, particularly targeting Facebook credentials and business accounts. Browser extensions can significantly enhance productivity by adding new features to web browsers like Microsoft Edge and Google Chrome. However, they also pose significant security risks, as malicious or compromised extensions can lead to data breaches, malware infections, and unauthorized access to corporate networks. It is crucial for organizations to control, block, or manage browser extensions to minimize security risks, particularly in an enterprise environment. This advisory outlines the steps to block and protect browser extensions for Microsoft Edge and Google Chrome, and it also includes specific guidance on managing extensions using Microsoft Intune.
Risks Associated With Browser Extensions
● Data Exposure: Some extensions can access sensitive data (e.g., browsing history, credentials, and files), potentially exposing confidential information.
● Malicious Extensions: Cybercriminals can create or compromise extensions, making them a vector for malware distribution or data exfiltration.
● Phishing Risks: Extensions may manipulate web content, tricking users into providing sensitive information.
● Performance Degradation: Some poorly coded extensions can slow down browsers or degrade system performance.
Managing Browser Extensions Using Group Policy
A. Microsoft Edge
Using Group Policy (Windows)
1. Open the Group Policy Management Console (GPMC).
2. Navigate to: Computer Configuration > Administrative Templates > Microsoft Edge > Extensions
3. Set the following policies:
a. Control which extensions are installed silently: Specify allowed extensions by adding their extension IDs.
b. Configure extension management settings: T o block all extensions, set this policy to "*" (deny all).
c. Configure the list of force-installed extensions: If any extension is necessary for business, add the corresponding extension ID here.
B. Google Chrome
Using Group Policy (Windows)
1. Open the Group Policy Editor.
2. Navigate to: Computer Configuration > Administrative Templates > Google > Google Chrome > Extensions
3. Set the following policies:
a. Block external extensions: Set the policy to block all extensions unless specifically allowed by adding the extension IDs.
b. Configure extension install allow list: If certain extensions are necessary, add their extension IDs here.
c. Configure extension install blocklist: Add a wildcard"*" to block all extensions.
Managing Browser Extensions Using Microsoft Intune
Organizations using Microsoft Intune for endpoint management can apply policies to control browser extension installations across all managed devices. This approach is particularly useful for managing large numbers of endpoints efficiently.
Blocking Extensions in Microsoft Edge Using Intune
1. Sign in to Microsoft Endpoint Manager Admin Center.
2. Navigate to: Devices > Configuration profiles > Create profile
3. Choose:
a. Platform: Windows 10 and later.
b. Profile type: Settings catalog.
4. In the Configuration settings, search for Extensions under Microsoft Edge:
a. Allow specific extensions to be installed (User): Specify allowed extension IDs
b. Control which extensions cannot be installed (User): Add a wildcard"*" to block all extensions.
5. Assign this profile to your target groups (specific users or devices).
Blocking Extensions in Google Chrome Using Intune
1. Sign in to Microsoft Endpoint Manager Admin Center.
2. Navigate to: Devices > Configuration profiles > Create profile
3. Choose:
a. Platform: Windows 10 and later.
b. Profile type: Settings catalog.
4. In the Configuration settings, search for Extensions under Google Chrome\Extensions:
a. Configure extension installation allow list (User): Specify allowed extension IDs
b. Configure extension installation blocklist: Add a wildcard"*" to block all extensions.
5. Assign this profile to your target groups (specific users or devices).
Note: These steps are mentioned for user-based controls. Similar configuration steps can be applied for device-based controls.
Best Practices for Managing Browser Extensions
● Audit Extensions Regularly: Regularly audit the extensions installed on users’ browsers to detect unauthorized or risky extensions.
● User Training: Educate users about the risks associated with browser extensions and how to identify malicious ones.
● Implement a Zero-Trust Model: Always assume that extensions can potentially be compromised. Apply the principle of least privilege when granting extension permissions.
● Use Security Solutions: Consider deploying security solutions that can monitor and block malicious browser activities, including suspicious extension behavior.
Conclusion
Controlling browser extensions in Microsoft Edge and Google Chrome is a critical aspect of securing enterprise endpoints. By implementing the steps outlined above, organizations can significantly reduce the risks associated with browser extensions. Whether you manage your endpoints using Group Policy or Microsoft Intune, these controls can help protect your network from potential extension-related threats. By following this advisory, organizations can take proactive steps to mitigate browser extension risks, enhancing their overall cybersecurity posture.
Reference:
https://www.bleepingcomputer.com/news/security/new-details-reveal-how-hackers-hijacked-35-google-chrome-extensions/
https://learn.microsoft.com/en-us/defender-endpoint/manage-profiles-approve-sys-extensions-intune
https://gbhackers.com/malicious-editthiscookie-extension/#google_vignette
Disclaimer
The information contained in this document is meant to provide general guidance and brief information to the intended recipient pertaining to the incident and recommended action. Therefore, this information is provided "as is" without warranties of any kind, express or implied, including accuracy, timeliness, and completeness. Consequently, under NO condition shall CTM360®, its related partners, directors, principals, agents, or employees be liable for any direct, indirect, accidental, special, exemplary, punitive, consequential, or other damages or claims whatsoever including, but not limited to: loss of data, loss in profits/business, network disruption…etc., arising out of or in connection with this advisory.
For more information:
Email: monitor@ctm360.com Tel: (+973) 77 360 360

CXO Fraud - Scam Emails Originating From Virgin Media, Optimum And Cox.Net
There is an ongoing scam email campaign targeting executives from prominent organizations around the world. These reported email addresses on the domains are genuine email accounts of 'Virgin Media', 'Optimum' & 'Cox communications' users' which are compromised and sold on underground forums. Scammers buy and use such accounts as they have a higher reputation compared to newly created free accounts to bypass email gateways and spam filters and also lower their risk of being detected or tracked back in a bigger BEC attack.
These accounts are compromised by threat actors via phishing emails and malware, and the issue with such accounts will persist as long as end users are not careful enough while dealing with phishing and malicious emails. Based on our previous experience in response with the hosts Virgin Media, Optimum and Cox.net which are TV and cable providers in the UK and USA. They do not investigate email accounts reported to their abuse team without the original email and header information as this is a mandatory requirement as per their abuse policies. However, once this information is provided they do take action by resetting/recovering the reported account of the original user.
Additionally, enabling strict quarantine measures on your email gateway from these domains will make you a harder target and eventually the attackers moving on to another one.
RECOMMENDATIONS
- As a precautionary measure, all email from private and/or external email addresses which contain the name of your executive staff in the "From" field may flagged.
- As part of containment, please ensure to quarantine emails from the domain @virginmedia[.]com, @optimum[.]net, @optonline[.]net, @cox[.]net, @cox[.]com
- As this type of email is tricky, it is highly recommended to conduct phishing awareness training for all employees to avoid potential risks.



